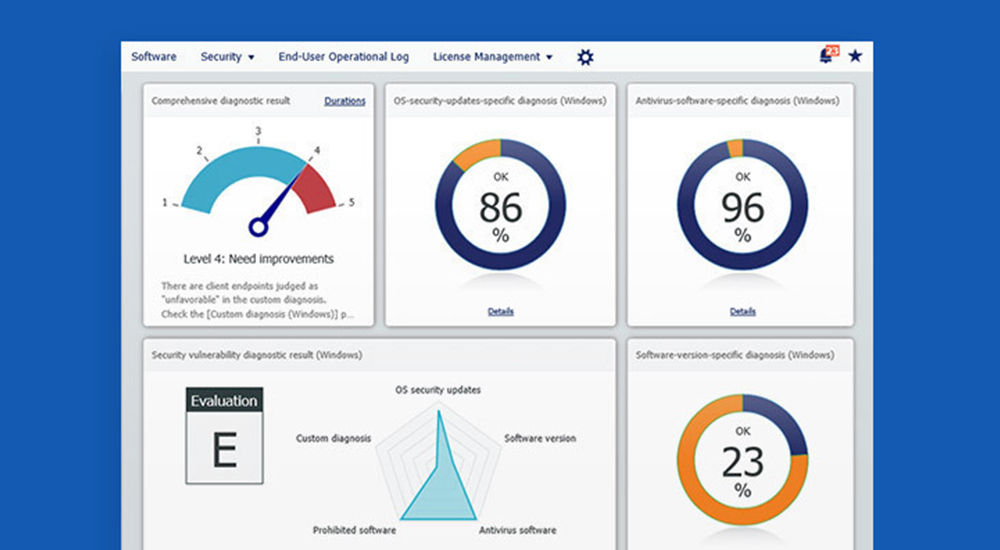
In recent years the business use of mobile devices such as smartphones and tablets has grown rapidly. Along with this growth, security risks such as device loss or theft and malware infection have also increased, making effective management and security measures for mobile devices an urgent priority for companies.
This article focuses on MDM (Mobile Device Management) as a means to address these challenges and explains its security features, the benefits of implementation, and key points for selecting a solution.